The Common Information Model (CIM) agent can be used to provide common building blocks to manage CIM-compliant devices.
Typical CIM agent configuration
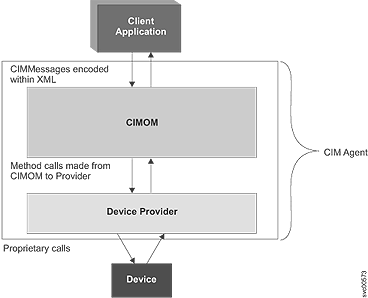
A typical configuration for your CIM client is to use the CIMOM that is at https://cluster_ip port 5989 with namespace=/root/ibm. The standard secure port is 5989. You can also use namespace=interop, which is the standard SMI-S namespace.
The client application sends CIM requests to the CIMOM. As requests arrive, the CIMOM validates and authenticates each request. It then directs the requests to the appropriate functional component of the CIMOM or to a device provider. To satisfy client application requests, the provider makes calls to a device-unique programming interface on behalf of the CIMOM.
The management application can obtain an instance of the RemoteServiceAccessPoint from the CIMOM. This instance is used by the management application to access the web user interface.
CIM agent configuration with Service Location Protocol
If you use Service Location Protocol (SLP) to discover the CIMOM, the client application locates the CIMOM by calling an SLP directory service. When the CIMOM is first invoked, it registers itself to the SLP Service agent and supplies its location, IP address, port number, and the type of service that it provides. A string that describes the CIM agent access point is registered.
service:wbem:https://<CIM Agent IP>:<port number>
template-type=wbem template-version=1.0 template-description=This template describes the attributes used for advertising WBEM servers. template-url-syntax=https://9.47.24.91:5989 service-location-tcp=https://9.47.24.91:5989 service-id=IBMTSSVC:9.47.24.91 ProtocolVersion=1.2 CommunicationMechanism=cim-xml FunctionalProfilesSupported=Basic Read, Basic Write, Instance Manipulation, Association, Traversal, Query Execution, Qualifier Declaration, Indications AuthenticationMechanismSupported=Basic Namespace=/root/ibm Interop=/interop MultipleOperationsSupported=false RegisteredProfilesSupported=SNIA:Storage Virtualizer, SNIA:Storage Virtualizer:Access Points, SNIA:Storage Virtualizer:Block Services, SNIA:Storage Virtualizer:Cascading, SNIA:Storage Virtualizer:Copy Services, SNIA:Storage Virtualizer:FC Initiator Ports, SNIA:Storage Virtualizer:FC Target Ports, SNIA:Storage Virtualizer:Health, SNIA:Storage Virtualizer:Masking and Mapping, SNIA:Storage Virtualizer:Multiple Computer System, SNIA:Storage Virtualizer:Physical Package, SNIA:Storage Virtualizer:Software, SNIA:Storage Virtualizer:Location, SNIA:Storage Virtualizer:Block Server Performance, SNIA:Storage Virtualizer:iSCSI Target Ports, SNIA:Storage Virtualizer:Disk Drive Lite, SNIA:Storage Virtualizer:Extent Composition, SNIA:Storage Virtualizer:Disk Sparing, SNIA:Storage Virtualizer:Thin ProvisioningSNIA:Array, SNIA:Array:Access Points, SNIA:Array:Block Services, SNIA:Array:Cascading, SNIA:Array:Copy Services, SNIA:Array:FC Initiator Ports, SNIA:Array:FC Target Ports, SNIA:Array:Health, SNIA:Array:Masking and Mapping, SNIA:Array:Multiple Computer System, SNIA:Array:Physical Package, SNIA:Array:Software, SNIA:Array:Location, SNIA:Array:Block Server Performance, SNIA:Array:iSCSI Target Ports, SNIA:Array:Disk Drive Lite, SNIA:Array:Extent Composition, SNIA:Array:Disk Sparing, SNIA:Storage Virtualizer:Thin Provisioning SNIA:Server,SNIA:Server:Profile Registration, SNIA:Server:Object Manager Adapter, SNIA:Server:Indication, SNIA:SMI-S
With this information, the client application starts to directly communicate with the CIMOM.
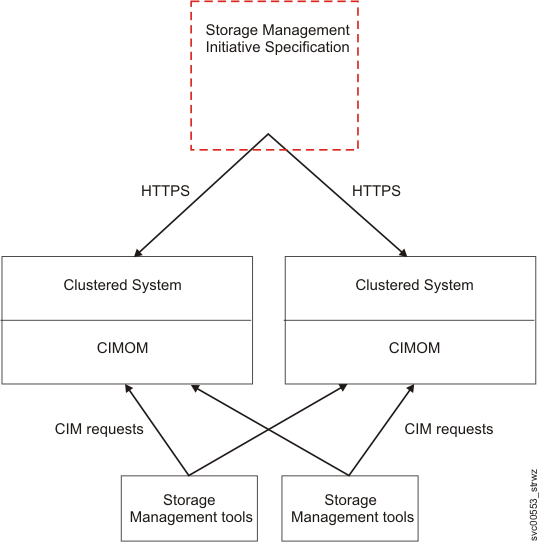
CIM agent configuration on the console and the clustered system
The CIMOM resides on theclustered system (system). The management GUIdoes not use the CIMOM that is on the clustered system. Other IBM storage management tools continue to use the CIMOM that is on the clustered system.