Mapping is the process of controlling which hosts or host clusters have access to specific volumes within the system.
Host mapping is similar in concept to logical unit number (LUN) mapping or masking. LUN mapping is the process of controlling which hosts have access to specific logical units (LUs) within the disk controllers. LUN mapping is typically done at the storage system level. Host mapping is done at the software level.
The act of mapping a volume to a host makes the volume accessible to the WWPNs or iSCSI names, such as iSCSI qualified names (IQNs) or extended-unique identifiers (EUIs) that are configured in the host object.
Volumes and host mappings
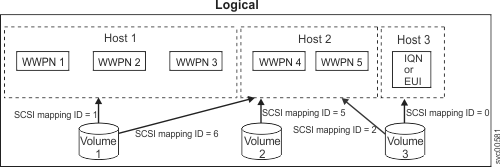
Each mapping associates a volume with a host or host cluster and provides a way for all WWPNs and iSCSI names in the host or host cluster to access the volume. You can map a volume to multiple hosts or host clusters. Mappings can either be shared or private. Shared mappings are volume mappings that are shared among all the hosts that are in a host cluster. When a host cluster is created, any common volume mappings become shared among all the hosts within the host cluster. If a mapping is not common, it remains a private mapping for that host only. Private mappings are mappings that are associated with an individual host. To view whether mappings are either private or shared mappings, select . The Mapping view displays all private mappings by default. From the view menu, select either Shared Mappings to view shared mappings for hosts or All Host Mappings to display all configured private and shared mappings. When a mapping is created, multiple paths might exist across the SAN fabric or Ethernet network from the hosts or host cluster to the nodes that are presenting the volume. Without a multipathing device driver, most operating systems present each path to a volume as a separate storage device. The multipathing software manages the many paths that are available to the volume and presents a single storage device to the operating system. If there are multiple paths, the system requires that the multipathing software run on the host or host cluster.
When you map a volume to a host, you can optionally specify a SCSI ID for the volume. This ID controls the sequence in which the volumes are presented to the host. Check the host software requirements for SCSI IDs because some require a contiguous set. For example, if you present three volumes to the host, and those volumes have SCSI IDs of 0, 1, and 3, the volume that has an ID of 3 might not be found because no disk is mapped with an ID of 2. The clustered system automatically assigns the lowest available SCSI ID if none is specified.
Figure 1 and Figure 2 show two volumes, and the mappings that exist between the host objects and these volumes.
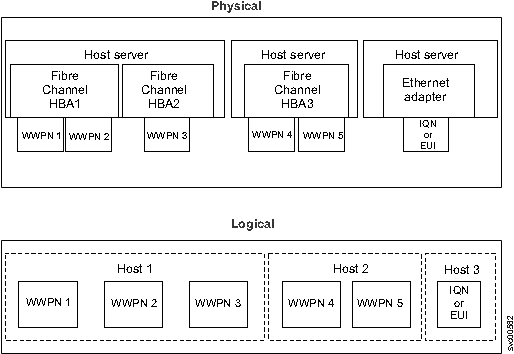
LUN masking is usually implemented in the device driver software on each host. The host has visibility of more LUNs than it is intended to use, and device driver software masks the LUNs that are not to be used by this host. After the masking is complete, only some disks are visible to the operating system. The system can support this type of configuration by mapping all volumes to every host object and by using operating system-specific LUN masking technology. However, the default, and recommended, system behavior is to map only those volumes that the host is required to access.